New malware targets Facebook, LinkedIn users
By Ajith Ram November 29, 2016
- Malware automatically downloads an image file
- Encrypts all files and demands a bitcoin ransom

ITs name sounds like the Norse god of mischief, but is far more sinister. A highly deceptive, but relatively simple malware is now spreading rapidly by exploiting vulnerabilities in Facebook and LinkedIn. Its high rate of infection during the last two weeks is worrying security researchers.
According to the security firm Check Point, there are serious security flaws in the coding of both Facebook and LinkedIn. This allows an infected image file to be downloaded onto the user's computer. If unwary users access the file, it will install the 'Locky' ransomware on their PCs.
Locky is not a new malware. It has been circulating since early this year. It encrypts the victim's files and demands a ransom of half a bitcoin for the unlock key. At current market rate, it is around US$365.
Before its recent propagation through Facebook and LinkedIn, Locky had used the macro function in Word and spam Emails. According to Check Point, there has been a "massive spread of the Locky ransomware via social media, particularly in its Facebook-based campaign."
At the moment, Check Point is not revealing the exact details of how Locky works using the social networks. They are waiting for the affected portals to fix the issue.
Facebook and LinkedIn users should not open any image file that has been automatically downloaded, particularly any image file with an unusual extension such as SVG, JS, or HTA. Although they may look innocuous, it might prove to be a ransomware.
According to researcher Lawrence Abrams, "when Locky encrypts a file it will rename the file to the format [unique_id][identifier].locky." It targets a large amount of file extensions and even more importantly, encrypts data on unmapped networks. Like the CryptoWall ransomware, Locky also completely changes the filenames for encrypted files to make it more difficult to restore the right data.
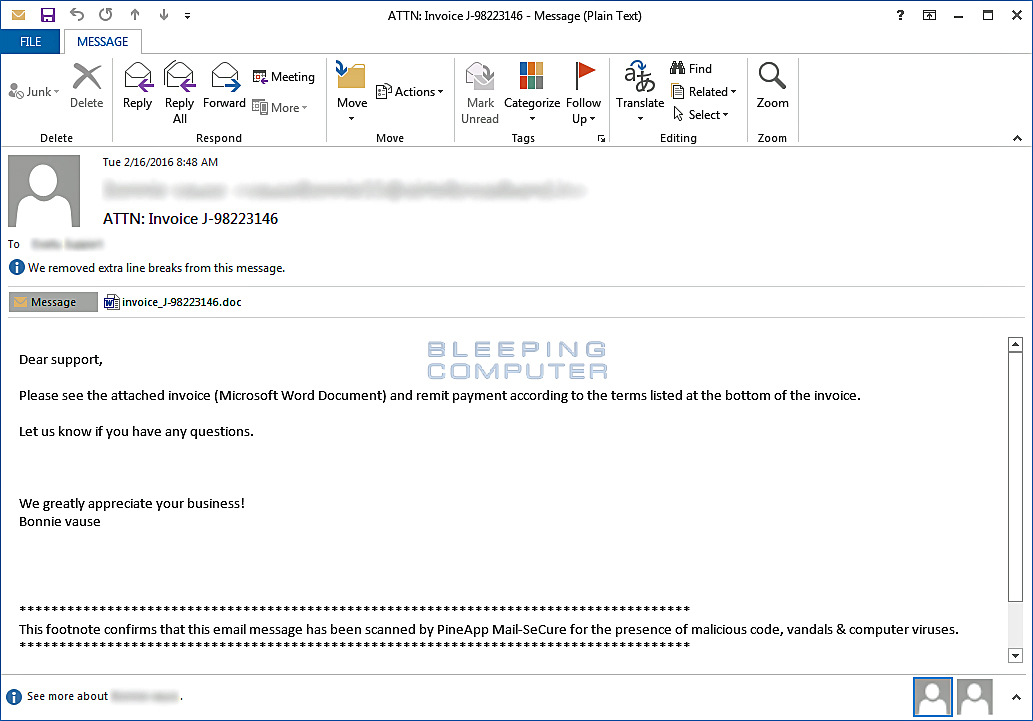
Before its current attachment to Facebook and LinkedIn, Locky was being distributed via email that contained Word attachments. The email message would contain a subject similar to ATTN: Invoice J-98223146 and a message such as "Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice".
According to Lawrence, Locky encrypts files on network shares even when they are not mapped to a local drive. System administrators should lock down all open networks and keep permissions to the barest minimum possible. As part of the encryption process, Locky will also delete all of the Shadow Volume Copies on the machine so that they cannot be used to restore the victim's files.
Check Point updated Facebook & LinkedIn of the attack vector early in September. As more people spend time on social networking sites, hackers have turned their focus to find a way in to these platforms. Cyber criminals understand these sites are usually ‘white listed’, and for this reason, they are continually searching for new techniques to use social media as hosts for their malicious activities.
Check Point recommends the following preventive measures:
a) If you have clicked on an image and your browser starts downloading a file, do not open it. Any social media website should display the picture without downloading any file.
b) Don’t open any image file with unusual extension (such as SVG, JS or HTA).
Related Stories:
Cybersecurity: Why sharing is more than just caring
Ransomware operators innovate to maintain profits
New security threat to Android devices
For more technology news and the latest updates, follow us on Twitter, LinkedIn or Like us on Facebook.


