The coming of the Personal Data Protection Act
By Edwin Yapp June 1, 2012
- Malaysia's Personal Data Protection Act comes into force in June
- Does not include mandatory obligation to notify public of security breaches
MALAYSIA has had for two years a Personal Data Protection Act (PDPA) gazetted in its laws but unbeknownst to many, the Act comes into force in June. So what exactly does the PDPA cover and how does it protect netizens and people in general?
 According to Teh Lip Guan (pic), executive director, PwC Advisory Services, the PDPA aims to protect the rights and freedoms of customers, known as data subjects, when used by companies – or data users - by defining the methods in which processing of the personal data is lawful.
According to Teh Lip Guan (pic), executive director, PwC Advisory Services, the PDPA aims to protect the rights and freedoms of customers, known as data subjects, when used by companies – or data users - by defining the methods in which processing of the personal data is lawful.
Teh says in the Malaysian context, one of the key challenges will be in data users clearly articulating to their data subjects the intent for which their data is being recorded.
“This means data subjects should be clearly informed about how the data user intends to use their personal data. If this isn’t made clear, the data subject may choose not to give his or her consent,” he says.
Woon Tai Hai, executive director of advisory and management consulting at KPMG, says there are seven principles (see chart, courtesy of KPMG) to the PDPA and that the processing of personal data by a data user must be in compliance with these principles.
In particular the “rights” of the customer in relation to personal data processing that one should be mindful of including: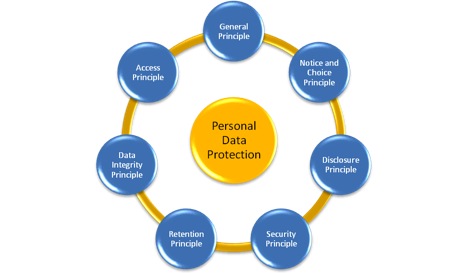
- Right of access to personal data;
- Right of amendments of personal data;
- Right to prevent processing of personal data for direct marketing purposes; and
- Right to withdraw consent processing of personal data especially if it can cause distress or damages.
Woon says, however, there are exemptions to these rights; for instance, when the personal data is processed by an individual for personal use, household or family affairs, when relating to a court order, and when relating to criminal investigations, including any directive from a Minister.
Under the microscope
As the PDPA comes into force this month, companies, especially those involved in the mining or capturing of personal data, will be under scrutiny because of the nature of the PDPA.
Woon says the key challenges encountered in compliance with the PDPA can manifest themselves in many forms and these include policies and supporting processes, systems and applications that need revamping to support the new processes, and changing the mindset of employees in processing these personal data.
 For instance, Woon (pic) says the financial services and telecommunication industries, which have undoubtedly collected and maintained high volumes of customer information including personal data over the years, may have to review their entire process-chain, including their customer relationship management (CRM) systems.
For instance, Woon (pic) says the financial services and telecommunication industries, which have undoubtedly collected and maintained high volumes of customer information including personal data over the years, may have to review their entire process-chain, including their customer relationship management (CRM) systems.
"Professionals such as executive search agencies and tax consultants are also vulnerable as personal data is often collected for the purpose of commercial transactions," he says.W
"Depending on the degree of compliance of the organization, such an exercise can be tedious and costly. However the penalty incurred and reputation of the company are perhaps more costly if breaches are subsequently discovered."
Woon however says that by far the biggest hurdle is whether companies already have systems and processes in place to meet the requirements of this Act, as the Government will argue that it has given ample time for companies to get ready.
PwC’s Teh notes that the issue of privacy continues to be a subject of great scrutiny in today's increasingly connected world.
Some common pitfalls include data users not being able to keep abreast of the many changes to the global regulation landscape which are happening in parallel, he adds.
As an extension to the challenge of a constantly evolving privacy landscape, Teh says the establishment of an internal informed source, particularly when overlapping legislations are in place, is also likely to be a challenge. “For example, when processing credit card transactions of healthcare institutions, both the Payment Card Industry Data Security Standard (PCI-DSS) and the Health Insurance Portability and Accountability Act (HIPAA) standards apply.”
Teh points out that the PCI-DSS standards aim to protect customer-sensitive information such as the name, card number and card verification value (or CVV), while the HIPAA aims to protect patient information such as eligibility to a health plan, premium payments, and so on.
“The common intent here is the preservation of the privacy of the data subject, but the organization’s application of controls will stretch to multiple departments and units internally where changes will need to be made to the respective processes and infrastructure.”
Mandatory revelation
Despite the PDPA having followed a good framework according to international standards, the Act could have included the mandatory notification requirements for data breach, says Ilias Chantzos, Symantec’s senior director of government affairs, Asia Pacific Japan.
 Speaking to Digital News Asia in an interview recently, Chantzos (pic) says that the PDPA follows the best practices of the seven data protection principles and is in line with other legislations seen in Europe and in the United States.
Speaking to Digital News Asia in an interview recently, Chantzos (pic) says that the PDPA follows the best practices of the seven data protection principles and is in line with other legislations seen in Europe and in the United States.
However, critical to the proposal that Symantec has seen across Europe and the United States is the built-in mandatory obligation to notify security breaches in their respective national data protection framework, he adds.
“If a company, for instance, loses data comprising those of its customers, employees, partners or any personal data that can be used to identify people, there must be a mandatory onus on it to report this loss to the national registration authority and the public at large," he says.
However, this Chantzos notes that this clause is not included in the PDPA. Asked why he thought this was so, Chantzos declines to speculate, only noting, “The justification [by some] sometimes could be that extra reporting may be over burdensome for companies to include such a clause in."
“Our view however is that companies must treat this with the utmost importance and should a company lose its data, they must notify the parties affected.”
Chantzos says that Symantec believes that in this information age, the need for breach notification is very real as evidenced by the staggering loss of millions of data records arising from several major data breaches occurring globally.
The information security player also believes that the threat of personal sensitive information such as financial, contact, employment information and other identity-related data being lost, stolen, accessed or disclosed without authorization, will only rise with the increasing reliance on advanced communication technologies for work-live-play and with individuals more frequently sharing their personal data.
Organizations also do not realize that handling data breaches has its costs, and these costs can be significant, Chantzos points out.
Additionally, Chantzos says the “breach notification” also has an important educational leverage for users and policy makers.
Symantec, he says, believes that such moves could raise general awareness and help individuals better understand how their personal data is protected online and what recourse they may have in case that data is disclosed without authorization.
Asked how else the public could be further educated on data protection, Chantzos says that it’s important to begin with a top-down approach and getting employees of all levels to explain to them the values of personal data protection.
“Begin by familiar electronic data protection principles, across the all levels of employees. This will help them gradually be aware that such legislation exists,” he says, adding that in time more people will be educated on the subject.


