42% surge in targeted attacks, small businesses have bullseye painted on
By Digital News Asia June 18, 2013
- Small businesses are attractive targets and a way in to ultimately reach larger companies via ‘watering hole’ techniques
- Consumers remain vulnerable to ransomware and mobile threats, particularly on the Android platform
 THE recent Symantec Corp Internet Security Threat Report, Volume 18 (ISTR) revealed a 42% surge during 2012 in targeted attacks globally compared with the previous year.
THE recent Symantec Corp Internet Security Threat Report, Volume 18 (ISTR) revealed a 42% surge during 2012 in targeted attacks globally compared with the previous year.
Designed to steal intellectual property, these targeted cyber-espionage attacks are increasingly hitting the manufacturing sector as well as small businesses, which are the target of 31% of these attacks, the company said in a statement.
Small businesses are attractive targets themselves and a way in to ultimately reach larger companies via ‘watering hole’ techniques. In addition, consumers remain vulnerable to ransomware and mobile threats, particularly on the Android platform.
“Cybercriminals aren’t slowing down; they continue to devise new ways to steal information from organisations of all sizes,” said Nigel Tan (pic, right), director of Systems Engineering, Symantec Malaysia.
“The sophistication of attacks coupled with today’s IT complexities, such as virtualisation, mobility and cloud, require organisations in Malaysia and globally to remain proactive and use ‘defense in depth’ security measures to stay ahead of attacks.
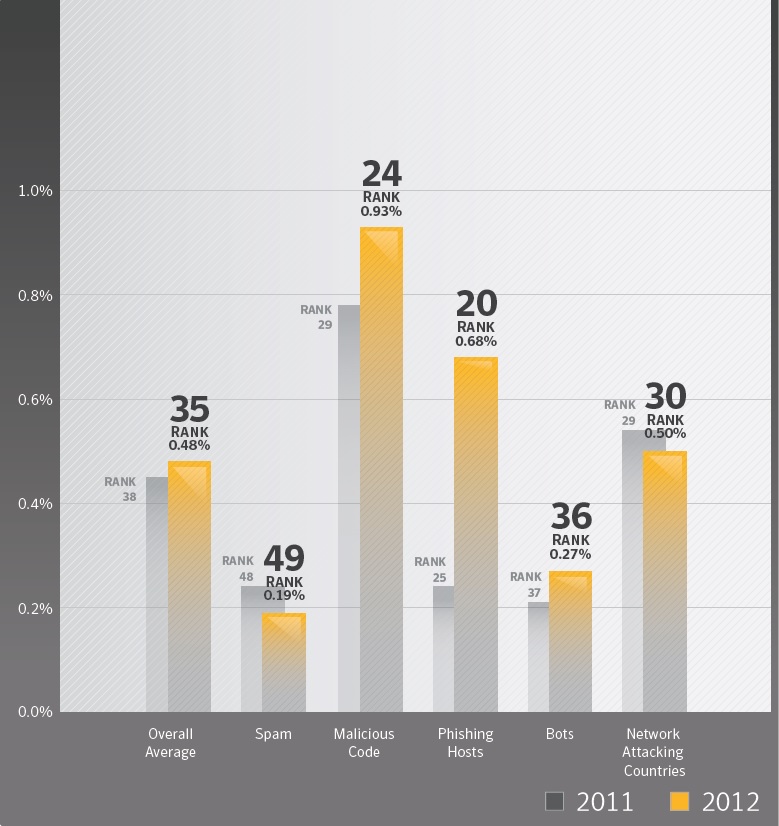
“While Malaysia is ranked 35th among countries globally on Internet threat activities, organisations should continue to take proactive initiatives to secure and manage critical information from a variety of security risks today.
“The top growing trends that organisations in Malaysia should watch out for in today’s threat landscape includes targeted attacks in the manufacturing and small businesses sectors, mobile malware, and phishing threats,” Tan added.
David Rajoo (pic above, left), senior technical consultant at Symantec Malaysia, said that cybercriminals are targeting customer information, financial details and intellectual property.
“They have more ways than ever to spy on us, through computers, mobile devices and social networks. Any information they glean, from banking details to email addresses of associates, can be used in stealing identities and crafting further sophisticated attacks.
“One of the most significant innovations in targeted attacks is the emergence of watering hole attacks. The attackers compromise the security of a website that an intended target is likely to visit and once the target visits the website, their computer becomes infected with malware,” he said.
 Path of least resistance (click chart to enlarge)
Path of least resistance (click chart to enlarge)
Targeted attacks are growing the most among businesses with fewer than 250 employees, according to ISTR 18.
Small businesses globally are now the target of 31% of all attacks, a threefold increase from 2011. While small businesses may feel they are immune to targeted attacks, cybercriminals are enticed by these organisations’ bank account information, customer data and intellectual property, Symantec said.
Attackers hone in on small businesses that may often lack adequate security practices and infrastructure.
Web-based attacks globally increased by 30% in 2012. Many of these attacks originated from the compromised websites of small businesses. These websites were then used in massive cyber-attacks as well as ‘watering hole’ attacks.
In a watering hole attack, the attacker compromises a website, such as a blog or small business website, which is known to be frequently visited by the victim of interest. When the victim later visits the compromised website, a targeted attack payload is silently installed on their computer.
The Elderwood Gang pioneered this class of attack; and, in 2012, successfully infected 500 organisations in a single day. In these scenarios, the attacker leverages the weak security of one business to circumvent the potentially stronger security of another business.
Manufacturing sector, knowledge workers
Shifting from governments, manufacturing has moved to the top of the list of industries targeted for attacks in 2012.
Symantec believes this is due to an increase in attacks targeting the supply chain – cybercriminals find these contractors and subcontractors susceptible to attacks and they are often in possession of valuable intellectual property.
By going after manufacturing companies in the supply chain, attackers gain access to sensitive information of a larger company.
In addition, executives are no longer the leading targets of choice. In 2012, the most commonly targeted victims of these types of attacks across all industries were knowledge workers (27%) with access to intellectual property as well as those in sales (24%).
Mobile malware and malicious websites
Last year, mobile malware increased by 58%, while 32% of all mobile threats attempted to steal information, such as e-mail addresses and phone numbers.
Surprisingly, these increases cannot necessarily be attributed to the 30% increase in mobile vulnerabilities.
While Apple’s iOS had the most documented vulnerabilities, it only had one threat discovered during the same period.
Android, by contrast, had fewer vulnerabilities but more threats than any other mobile operating system. Android’s market share, its open platform and the multiple distribution methods available to distribute malicious apps, make it the go-to platform for attackers.
In addition, 61% of malicious websites are actually legitimate websites that have been compromised and infected with malicious code. Business, technology and shopping websites were among the top five types of websites hosting infections.
Symantec attributes this to unpatched vulnerabilities on legitimate websites. In years past, these websites were often targeted to sell fake antivirus to unsuspecting consumers. However, ransomware, a particularly vicious attack method, is now emerging as the malware of choice because of its high profitability for attackers.
In this scenario, attackers use poisoned websites to infect unsuspecting users and lock their machines, demanding a ransom in order to regain access.
Another growing source of infections on websites is malvertisements—this is when criminals buy advertising space on legitimate websites and use it to hide their attack code.
The Internet Security Threat Report provides an overview and analysis of the year in global threat activity. The report is based on data from Symantec’s Global Intelligence Network, which the comoany’s analysts use to identify, analyse, and provide commentary on emerging trends in attacks, malicious code activity, phishing, and spam.
Related Stories:
Malware targeting small businesses: Symantec report
IM the weakest link in security, says Symantec survey
Mobile malware threats on the rise
For more technology news and the latest updates, follow @dnewsasia on Twitter or Like us on Facebook.


