HP gets serious about security, controversial Autonomy deal bearing fruit
By A. Asohan March 11, 2013
- Brings together various security teams together to form new unit, the HP Security Research (HPSR) organization
- Aiming for series of product roll-outs, including new technologies that integrate assets from controversial Autonomy deal
 WITH all the backlash from Hewlett-Packard’s now-controversial acquisition of Autonomy Corp – the subject of alleged financial impropriety, threatened lawsuits and UK regulator investigation – it is easy to forget that once, not so long ago, the only question that arose was the US$11-billion price HP paid for it in 2011.
WITH all the backlash from Hewlett-Packard’s now-controversial acquisition of Autonomy Corp – the subject of alleged financial impropriety, threatened lawsuits and UK regulator investigation – it is easy to forget that once, not so long ago, the only question that arose was the US$11-billion price HP paid for it in 2011.
Beyond that overly-hefty price tag, the acquisition made business and technology-integration sense. Indeed, HP has just begun making major harvests from that deal, integrating Autonomy assets into part of the company’s latest and most significant move in the information security space.
“I’ll tell you what we’ve done with Autonomy technology, and you tell me whether it is any good,” chuckled Paul Muller (pic), IT management evangelist at HP Software, when Digital News Asia (DNA) asked him at a recent media briefing in Kuala Lumpur if the Autonomy acquisition had been good for anything.
The big news, on the positive side of the scale at least, is that the company has brought together all the various teams and units it has had working on security to form the HP Security Research (HPSR) organization, which also released its inaugural annual Cyber Security Risk Report.
The new organization “will provide actionable security intelligence through published reports, threat briefings and enhancements to the HP security product portfolio,” the company said in a statement.
As part of the HP Enterprise Security Products (ESP) business unit, HPSR will lead the company’s security research agenda, leveraging existing HP research groups, including HP DVLabs or ‘digital vaccine’ research organization that is focused on vulnerability discovery and analysis; HP Fortify Software Security Research, which develops software security practices; and HP’s Zero Day Initiative (ZDI) team, which identifies software flaws that have led to cyber-attacks and security breaches.
“(Security) is not an area we play in, it’s an area we’re committed to,” said Muller. “There were all these different teams, but to be fair, they were not coordinated. HPSR brings them all together.”
“And now, we’re going to turn that insight we gain into action. It’s not pure research anymore. We’re bringing all the other parts of HP into the security organization, which gives us a really strong portfolio in the areas we’re focused on, which are software security assurance, security information, event management and intrusion.
“Today’s announcement is part of an ongoing series of innovations we’re going to be rolling out,” he added.
The threat landscape
Muller said that HP’s security move stems from the fact that it is “deeply embedded in some of the largest companies of their kind across the world.”
“In the area of financial services, the majority of Wall Street banks rely on us to keep them from harm on a daily basis; software vendors look to us to help them test and look for vulnerabilities in their source code; telecom providers; and in fact, the US military relies on us across all its defense forces and intelligence agencies,” he said.
HP’s security rollout is focused on three strategic areas which are of concern to its customers, Muller said.
“First of all, it’s ‘hardening the attack surface’ – the various windows, doors, locks that the bad guys are using to get into enterprise data and enterprises systems today,” he said. “Attack surfaces include everything from applications to infrastructure.”
“Every time you add a new database, application or mobile device, you’re exponentially increasing the number of avenues or entry points,” he said, explaining that it was not just the number devices or portals a company added, but also the various inter-connections and interactions between the two that added to the vulnerability quotient.
HP believes security is not an issue that can be resolved by looking at one product, or two – which is what the software security industry is all about.
“Our experience is that it takes more than one product to solve a problem, so our approach is to start by hardening the infrastructure itself,” said Muller. “We work with our PC and server teams, and our networking and storage teams, to harden the underlying infrastructure. We also work with our software teams to harden the next level.
“Each of these levels requires cooperation across multiple disciplines and silos. Let’s face it, we’re facing a very sophisticated enemy, and we need a very sophisticated response.
“This is very critical: It’s really tough to generalize solutions to security problems. In fact, it is dangerous to do so,” he said.
No more Dr No
The second strategic area is risk management, Muller said, noting that security organizations are often looked at by the business people who fund them as a necessary evil.
“In fact they’re often seen as the ‘innovation-prevent division,’ or ‘Dr No’,” he pointed out. “Every time you want to do something, they say ‘No,’ on account of the security risk it may bring.
“The challenge today for security professionals and chief information security officers is how to create a risk-enabling environment, where they can take a necessary amount of risk that is managed, rather than seek to prevent all possible risk.
“You cannot create a completely safe system. You will be penetrated; it’s a question how quickly you can identify the risk, shut it down and take strategic action to prevent it in the future.
The third strategic area is proactively identifying risk and taking action to prevent it. “That’s a science in and of itself,” he added.
New products, and Autonomy
Muller noted that large enterprises can afford to have whole teams dedicated to security. “They’re just as vulnerable as the little guy, who can’t even afford an IT person let alone entire dedicated security teams, but whose information is just as valuable to the bad guys.”
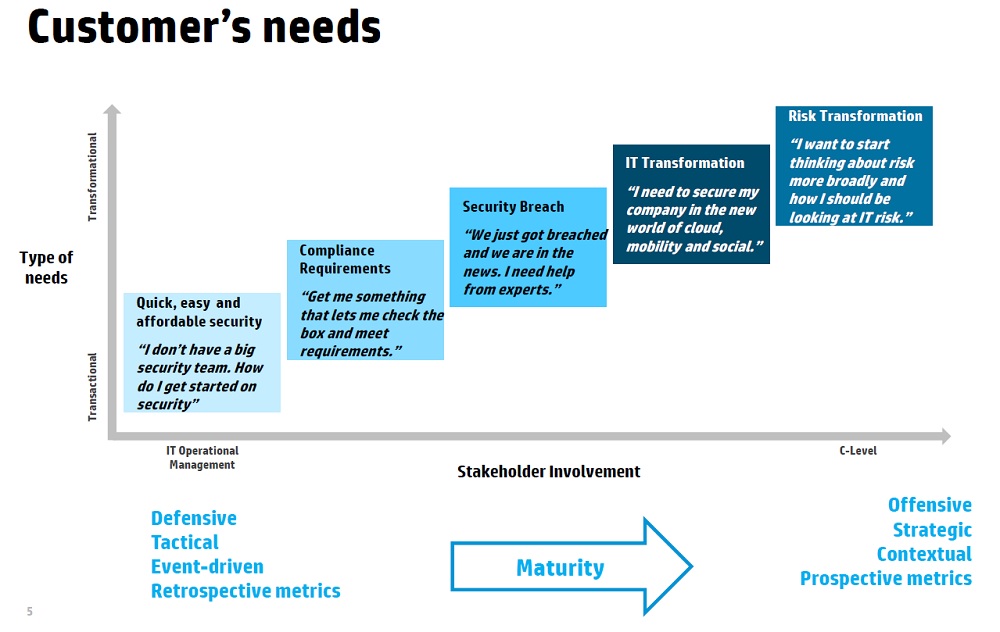
HP calls this the maturity curve, from companies which require quick, easy scalable solutions that can be deployed right now, right up to risk transformation, where risk is looked upon as an enabler and not the “innovation-prevention” unit.
“You’ve got to find the right solution to the right problem -- which the customer can actually use,” he said.
As part of its security product roll-out, the company has enhanced its HP Reputation Security Monitor (RepSM) 1.5, which protects clients against advanced threats by leveraging data feeds directly from HPSR.
These data feeds enhance the identification of peer-to-peer network use and improve detection of potential spear phishing and spam floods, while also recognizing patterns over time, such as reconnaissance scans and abnormal activity levels.
“Reputation is a very important part of what it means to be a chief information security officer today, and what I mean by that is you may discover some suspicious activity between your system and outside destination,” said Muller
“You may get worried – but you don’t really know until you know the reputation of that destination,” he added.
The new HP RepSM enables clients to defend against sophisticated attacks by detecting dangerous interactions with ill-reputed sites to prevent a breach. After a breach occurs, the solution identifies the infected assets, communicating with ill-reputed command and control centers, before intellectual property is leaked, according to HP.
One of the biggest technology trends of recent times is big data, where all the unstructured data out there – from the Web and social media, amongst other sources – is being treated to the same kind of rigorous collation and analysis that traditional data residing in structured databases have always been subject to.
“Which brings me to my next point: Big data = big threat, because if you put all your information into one easy-to-consume package for your business, guess what? You’ve got an easy-to-consume package for all the bad guys as well,” said Muller. “Security through obscurity sometimes works.”
“What we’re doing is to integrate Autonomy assets that we acquired about 12 months ago, which is all unstructured data tools, to create a new type of security solution which does sentiment analysis,” he added.
With this, organizations can automatically apply sentiment analysis and event information to their big data and security event platforms to gain real-time visibility into the internal and external threat landscape, HP said.
The company said it has integrated the security information and event management (SIEM) capabilities of HP ArcSight with the HP Autonomy IDOL content analytics engine. This combination automatically recognizes the context, concepts, sentiments and usage patterns related to how users interact with all forms of data.
“With big data, the bad guys have only one place to go. You have two problems: How do you understand what’s inside there; and two, how do you understand patterns of activity without having to put people in there to look at each activity?” said Muller.
The new solution broadens the reach of an organization’s security monitoring capabilities by bringing meaning to raw security data. By enabling the tracking and analysis of human sentiments associated with data, such as behavior patterns, organizations are better equipped to quickly identify threats that would have previously gone unnoticed, HP claimed.
The company also announced a new plugin-ready platform, the HP ArcSight/Hadoop Integration Utility that it said seamlessly integrates HP ArcSight 6.0c with Apache Hadoop. Together, the technologies speed the process of digging through big data stores to provide a more complete view into events and to more quickly identify security attack trends.
 The solution links HP ArcSight’s reporting, search and correlation capabilities with Hadoop’s large, centralized storage repository, giving organizations the storage capacity needed to handle petabytes of information.
The solution links HP ArcSight’s reporting, search and correlation capabilities with Hadoop’s large, centralized storage repository, giving organizations the storage capacity needed to handle petabytes of information.
Open-source machine-learning algorithms, statistical analysis, anomaly detection and predictive analytics can be applied to the stored data, providing greater insight and resolution into security events, HP said.
For the lower end of HP's “maturity curve” model (click chart to enlarge), the company announced HP ArcSight Express 4.0 which it claimed simplifies the collection, analysis and management of security events quickly and cost-effectively.
“How do I get enterprise-quality security intelligence in an easy-to-consume package for small and medium businesses (SMBs) so I don’t need a 1,000 people to properly integrate it?” said Muller.
For midmarket organizations with large volumes of data and limited resources, HP ArcSight Express 4.0 combines SIEM, log management and user activity monitoring in an out-of-the-box solution, including connectors to HP ArcSIght IdentityView and HP RepSM.
Clients can be up and running in minutes, quickly gaining insight into potential security threats by pulling information from hundreds of data sources. The solution also monitors user and application activity for security anomalies, such as suspicious behavior.
HP RepSM 1.5 will be available worldwide on March 31. HP ArcSight Express 4.0 will also come with a free trial version of HP RepSM. ArcSight Express is priced at US$45,000 and up.
Cloud security
While cloud adoption is picking up pace, there are still some organizations holding back for a variety of reasons, most of them revolving around security and data sovereignty, the latter including regulatory reasons for certain industries like banking and finance for which there are limitations as to where data can be hosted.
But there is also some degree of nervousness, noted Muller. “The same firewalls that are keeping the bad guy out is also keeping you from seeing what is happening inside. That’s a problem, because all your customer or sales information is in there (in the cloud), and you may want to know who’s looking at all this.”
Such firewalls are opaque, so what HP has done is to build what Muller calls a “set of x-ray goggles for chief information security or chief risk officers to see behind the firewall your cloud provider has put up.”
The HP ArcSight Cloud Connector Framework allows organizations to easily collect application event and log data from cloud service providers. It comes in the form of application programming interfaces or APIs to be released by the provider, and HP is working hard on making the Cloud Connector Framework an industry standard.
“Salesforce.com was our initial R&D partner in this. We’ve also done a reference implementation with Box and Google,” said Muller. “We’re looking to implement this across the industry.”
He said that HP is also working on other aspects of cloud security and is a board member of the Cloud Security Alliance, a not-for-profit organization led by a broad coalition of industry practitioners, corporations, associations and other key stakeholders.
Next up: The security report – it’s scary out there
Related Stories:
Time will tell with HP's rediscovery
Cloud use in SEA facing 'rogue cloud' challenge: Symantec
Security on the cloud: Myths dispelled
For more technology news and the latest updates, follow @dnewsasia on Twitter or Like us on Facebook.


