Unknown traffic bigger security threat than social media: Page 2 of 2
By Gabey Goh May 28, 2013
Asia Pacific enterprises still maturing
When asked what the maturity level was in the Asia Pacific region regarding network security approaches, Brazil said that it was definitely evolving although the maturity level “isn’t quite there yet.”
He said a lot of companies here follow what they define as ‘best practices’ such as firewalls and firewall helpers, which are not used in other regions such as North America.
“Even though customers in Asia are using firewall helpers, none are really integrated together with the rest of the network and [this] provides a false sense of security. In addition, this traditional approach to security isn’t equipped to handle new types of attacks,” he said.
“It’s those attacks that companies in North America are more sensitive to, but we are seeing the same starting to happen with Asia Pacific companies as well,” he added.
When asked about what upcoming trends will be dominating security conversations in the coming months, Brazil identified a few areas.
Firstly the decryption of SSL traffic is increasing in importance, as it accounts for a big block of network traffic with IT administrators having no access into what it contains.
Secondly, virtualised network security will continue to dominate discussions as companies seek to protect and manage the growth of east-west traffic across networks.
“The other thing is orchestration. That’s the Achilles heel of cloud computing at the moment -- you can create applications quickly but then have to put brakes to wait for the change in security policies. So being able to pull in firewall policy into orchestration is going to be huge,” said Brazil.
Another trend is the shift to an extended network model in reaction to the proliferation of mobile devices accessing corporate networks, allowing users consistent and secured access to applications based on the assumption that they are 'always on' the network regardless of location.
Lastly, the prominence of the BYOD (bring your own device) trend will uncover the need for user and application visibility for network administrators as the key concern becomes not what devices employees are bringing in, but what applications are being accessed on them instead.
“These are the current challenges that we foresee becoming more fleshed out, beyond the questions people are asking today,” he said.
Palo Alto Networks has also compiled a quick list of recommendations for enterprises seeking to better secure their networks:
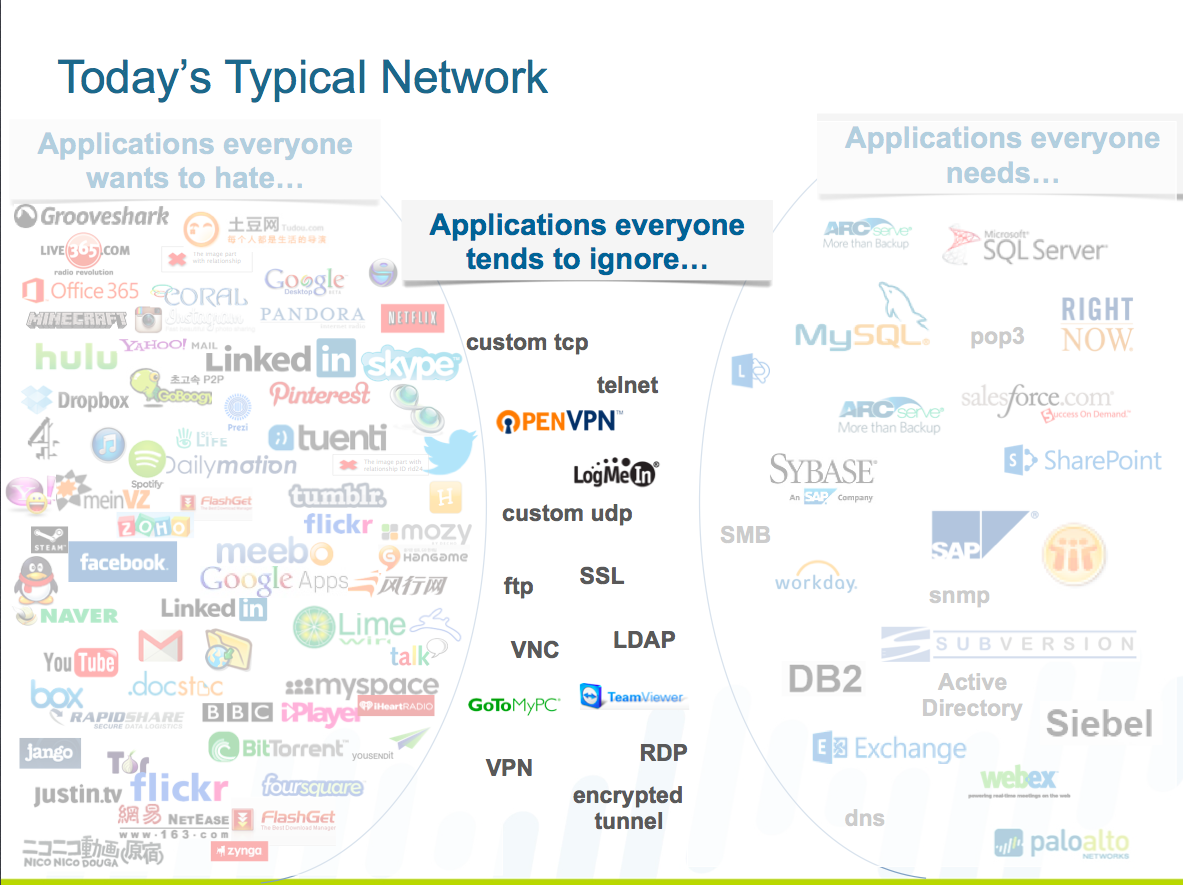 For third party applications:
For third party applications:
- Balance security and application access.
- Ask what is the business use for an application before allowing access.
- Apply quality of service (QoS) to video applications.
- Block Facebook apps without impeding social media initiatives.
For business applications:
- Isolate internal applications; monitor for rogue application use (SSH, RDP, etc).
- Allow specific users to access specific applications.
- Apply threat prevention.
For network/administrative applications:
- Reduce the volume of traffic and associated risks.
- Identify and isolate internal applications.
- Determine which applications might be commercial but not yet identified.
The 10th edition of the Palo Alto Networks Application Usage and Threat Report released in February 2013 uses data collected between May and December 2012 from application traffic analysis conducted across 3,000 organisations worldwide.
To view visual representations of the results or download the report in full, click here.
Related stories:
Cyber-war: Staying clear of DDoS attacks
Infoblox tackles DNS security, eyes Malaysian market
Are mobile networks as safe as we think?
For more technology news and the latest updates, follow @dnewsasia on Twitter or Like us on Facebook.


