It’s a BYOT (bring your own trouble) world: Fortinet report
By Digital News Asia September 5, 2013
- FortiGuard team seeing more than 1,300 new samples of mobile malware per day
- Attackers taking advantage of old vulnerabilities, despite patches being available
AS more people get mobile devices for both work and play, the amount of mobile malware has gone up and cybercriminals are increasingly targeting slack mobile security policies in the workplace.
Even the financially lucrative ransomware – malware that holds a user’s data or infected system for ransom, unless the perpetrator is paid off – is making its way to the mobile platform, according to the latest report by network security specialist Fortinet.
The company recently announced the findings of its FortiGuard threat landscape research for the period of Jan 1 to July 31, 2013.
1) Mobile malware on the rise
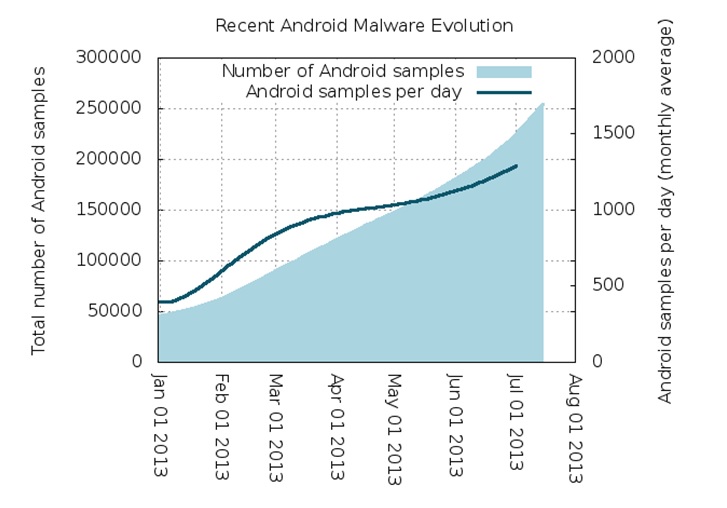
FortiGuard Labs observed a 30% increase in mobile malware in the labs over the last six months. The team is now seeing more than 1,300 new samples per day, is currently tracking over 300 unique Android malware families and over 250,000 unique malicious Android samples.
Figure 1 below shows the increase in mobile malware from January, 2013 through July, 2013.
2) Bring Your Own Trouble
The Bring Your Own Device (BYOD) phenomenon has many benefits for a business, chief among them are increased employee efficiency and productivity gains, Fortinet said in a statement.
However, the disadvantage of a lenient BYOD policy is the threat of mobile malware infecting the user’s device and, subsequently, the business network.
“Three years ago, mobile malware wasn’t much of a concern for users or businesses. Most malware at the time targeting smartphones and tablets were nothing more than ‘annoyware’ such as the Cabir virus or scam software used to commit SMS fraud or replace icons,” said Axelle Apvrille, senior mobile antivirus researcher for Fortinet’s FortiGuard Labs.
“However, as devices have proliferated, so, too, have cybercriminals eager to capitalise on the growing user base, and our research shows the proliferation of mobile malware will not abate anytime soon,” she said.
 3) 2013 changed the mobile threat landscape
3) 2013 changed the mobile threat landscape
In 2013, the mobile threat landscape changed dramatically. Wide scale manufacturer adoption of Google’s Android OS (operating system) globally has led to an explosion of smartphones in the marketplace.
Android devices are available in every market, at price levels from the incredibly inexpensive to feature-rich, cutting edge computing monsters.
Coupled with the explosion of available applications to extend device functionality, cybercriminals and other nefarious types have used this platform as a new business opportunity.
4) Mobile ransomware has its coming-out
In 2012, FortiGuard predicted that the financially lucrative ransomware would make its way onto mobile phones.
“Ransomware has been incredibly successful financially for cybercriminals, it’s no surprise they’ve turned their attention to mobile devices,” said Richard Henderson, security strategist for Fortinet’s FortiGuard Labs.
“The Fake Defender malware for Android follows the same MO (modus operandi) as PC fake antivirus software – it pretends to be altruistic, but in reality, it lies in wait to launch its true form.
“This malware then locks the victim’s phone and demands payment before unlocking the device. Once the phone is locked, the victim can either pay the ransom or completely erase their device, losing all their photos and data unless they have a full backup elsewhere,” he said.
5) New attacks on old vulnerabilities
Even though there have been recent patches for Ruby on Rails, Java, Adobe Acrobat and Apache, FortiGuard Labs is finding attackers are still exploiting those old vulnerabilities.
6) Ruby on Rails
In January 2013, it was announced that a critical vulnerability in the Ruby on Rails Framework could allow a remote attacker to execute code on the underlying Web server.
Ruby on Rails (RoR) is a Web application framework for the Ruby programming language. Put simply, it allows for rapid, easy and elegant deployment of ‘Web 2.0’ websites. RoR is a popular framework; hundreds of thousands of websites online use RoR in some fashion.
Further adding to the problem, a Metasploit module was made available to scan for the vulnerability, making the ability to find a Web server to exploit a trivial matter.
7) Java remote code execution
In January 2013, a zero-day exploit that was able to bypass Java’s sandbox and run arbitrary Java code was discovered.
Java is a ubiquitous technology online – most computers have some form of Java installed and enabled. The vulnerability allowed a malicious applet to run any Java program, bypassing Java’s sandbox and granting full access to the vulnerable computer.
Attacks were discovered in the wild and the exploit was quickly integrated into many popular crimeware attack kits, such as BlackHole, Redkit and Nuclear Pack, giving purchasers of these kits the ability to take advantage of the exploit and install malware on computers.
A Metasploit module was also created for the vulnerability, making the ability to find victims a simple point and click affair.
8) Acrobat/ Acrobat Reader zero-day in the wild
In February 2013, a PDF pretending to be a travel visa form from Turkey was detected circulating in the wild and took advantage of a previously unseen vulnerability in Adobe’s Reader software. The exploit worked with all recent versions of Adobe Reader (9.5.X, 10.1.X, and 11.0.X), and on most versions of Microsoft Windows, including 64-bit Windows 7 and most Mac OS X systems.
The exploit PDF was used by cybercriminals in order to install malware on their target’s computers.
9) CDorked attacks Apache
In late April 2013, a new attack on the popular Apache Web server was discovered. Dubbed CDorked, the malware was able to compromise the Web server and redirect visitors of the compromised Web server to other servers that deliver malware using the BlackHole exploit kit. The attack may also have targeted the Lighttpd and Nginx Web server platforms.
Related Stories:
Unknown traffic bigger security threat than social media
‘You may never want to go online again’
42% surge in targeted attacks, small businesses have bullseye painted on
Big data approach can help shore up cyber-defence: RSA
For more technology news and the latest updates, follow @dnewsasia on Twitter or Like us on Facebook.


